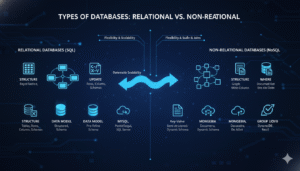
The SQL Application’s primary features include the following.

- In relational databases, data tables are manipulated utilizing SQL programs. It enables you to input table data, update data from previous sql tables, delete unnecessary table data, and generate data from one or more new sql tables.
- To get data from a single or several databases or SQL tables, SQL offers a variety of procedures. It enables you to aggregate table records based on particular criteria, show table records, filter table records, and sort database table records in ascending and descending order.
- The database structure is defined using the SQL program. Including tables, columns, and relationships between tables that are internal and external. You can make changes to databases, delete database tables, and create database table objects.
- Several commands are available in SQL to manage access to database data. You may provide or take away rights from users and groups using this tool.
- Processing transactions is supported by SQL. It guarantees the consistency, isolation, and durability of database operations.
- You may index database records using SQL to construct tables. This may enhance the efficiency of searches that access the data.
- SQL has a number of procedures to combine data from different tables based on shared fields.
- Views, which are essentially virtual tables, are possible with SQL. Can rely on a single or a number of SQL tables. Table views may add an amount of transparency to the underlying data and can simplify difficult queries.
- You can develop stored procedures with SQL. Which are precompiled portions of code that the database server is capable of running. By minimizing the amount of information sent between the client and the server, stored processes can enhance performance and security.
- Triggers may be made using SQL. Which are certain subcategories of stored processes. Which, in reaction to certain database events like inserts, updates, and deletions, are automatically carried out. Business rules may be maintained and data integrity can be maintained via triggers.